In today’s connected world, it is crucial to safeguard your digital assets and keep your information private. RDnetra has committed to build and shelled a security zone for our customer’s user to work globally and remotely hassle free and protect your online identity and guaranteeing the privacy, accuracy, and accessibility of your data.
- Network Security: We design, implement, and manage powerful network security solutions that shield your business from intruders, data breaches, and other network-related threats. Our team of professionals guarantees the security and integrity of your network traffic while preserving maximum network efficiency.
- Endpoint Security: To defend your devices, including desktops, laptops, and mobile devices, against malware, ransomware, and other malicious assaults, we implement cutting-edge endpoint security solutions. We offer antivirus software, advanced threat detection, and pro-active vulnerability management as part of our solutions.
- Cloud Security: As organizations increasingly rely on cloud services, we ensure your data stored in the cloud remains safe. Our cloud security solutions encompass data encryption, access controls, and continuous monitoring to safeguard your assets.
- Mobile Device Security: Securing mobile devices is essential given their widespread use. To safeguard your sensitive information and stop unauthorised access, we put strong security measures in place for smartphones, tablets, and other mobile devices.
- Data Loss Prevention (DLP): Data security must be a top priority. We implement cutting-edge DLP solutions that track, identify, and stop unauthorised data transfers, whether malicious or unintentional. Our DLP systems assist you in complying to data protection laws and avoiding data breaches.
- Identity and Access Management (IAM): Our IAM solutions help you establish strong control over user access to your systems and sensitive data. We implement multi-factor authentication, role-based access controls, and identity governance frameworks to ensure that only authorized personnel can access critical resources.
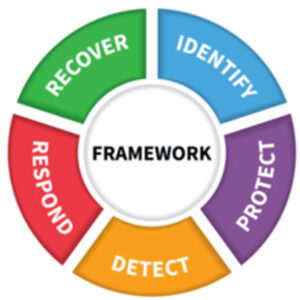
We help to Build A 5-Phase Cybersecurity Lifecycle Framework for Your Business
- Identify
- Protect
- Detect
- Respond
- Recover
